41 | Add to Reading ListSource URL: www.nymir.orgLanguage: English - Date: 2010-06-10 10:06:15
|
|---|
42 | Add to Reading ListSource URL: www.alaska.eduLanguage: English - Date: 2015-01-22 19:30:07
|
|---|
43 | Add to Reading ListSource URL: info.alaska.eduLanguage: English - Date: 2015-01-22 19:30:07
|
|---|
44 | Add to Reading ListSource URL: www.djoglobal.comLanguage: English - Date: 2014-12-30 13:35:25
|
|---|
45![Microsoft Word - EPJ_Laptop_Policy[removed]short.docx Microsoft Word - EPJ_Laptop_Policy[removed]short.docx](https://www.pdfsearch.io/img/3dbf041c8e1d443f4d1dfab015723bcd.jpg) | Add to Reading ListSource URL: epj.squarespace.comLanguage: English - Date: 2012-07-30 21:43:31
|
|---|
46 | Add to Reading ListSource URL: www.maccae.orgLanguage: English - Date: 2014-12-05 07:08:36
|
|---|
47 | Add to Reading ListSource URL: www.albertahealthservices.caLanguage: English - Date: 2014-10-31 13:16:56
|
|---|
48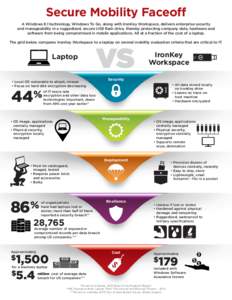 | Add to Reading ListSource URL: blog.ironkey.comLanguage: English - Date: 2014-02-19 10:50:36
|
|---|
49 | Add to Reading ListSource URL: www.nait.caLanguage: English - Date: 2012-01-13 14:36:19
|
|---|
50 | Add to Reading ListSource URL: www.timeincnewsgroupcustompub.comLanguage: English - Date: 2010-08-30 15:31:32
|
|---|